(Network Administrators (Persian
نکات مهم شبکه برای متخصصین(Network Administrators (Persian
نکات مهم شبکه برای متخصصینپیکربندی سویچ برای بالا بردن امنیت در لایه 2
Configure Your Catalyst for a More Secure Layer 2
IP Source Guard and Port Security
Using just DHCP snooping, you have stopped untrusted devices from acting as a DHCP server; which is important in an environment where people think it's a good idea to bring in their Linksys access point to better cover the office with wireless. Port Security can also help to stop more than one MAC from being seen on a port, making it impossible to connect hubs and other network-extending devices.
Now, to stop malicious people from using IP addresses that weren't assigned to them, we use IP source guard. Even better, we can also stop clients from forging their MAC address. MAC address filtering makes flooding the switch impossible. Flooding is a technique by which an attacker sends so many MAC addresses from their port that the switch's MAC table overflows. Then the switch has no choice but to flood all Ethernet frames out of every single port, since it doesn't know what MAC is connected where, allowing an attacker to see all the traffic across the switch. Some viruses have been known to do this as well.
ادامه مطلب ...Transparent Cisco IOS Firewall(ترجمه فارسی بزودی در همین وبلاگ)
Transparent Cisco IOS Firewall
Cisco IOS routers can be configured as a layer 2 bridges, this means that you can configure two or more interfaces to be in the same layer 2 domain and that traffic will be switched instead of routed. Another feature that has been added since IOS 12.3(7)T is the transparent Cisco IOS Firewall. This allows traffic filtering and stateful inspection using CBAC for the layer 2 bridge.
When you configure the router as a transparent firewall it will not do any routing and will only learn the MAC addresses on the interfaces and switch frames between the interfaces. The advantage of a transparent firewall is that you can place it at any location in your network without having to change any IP addresses or networking settings like default gateways.
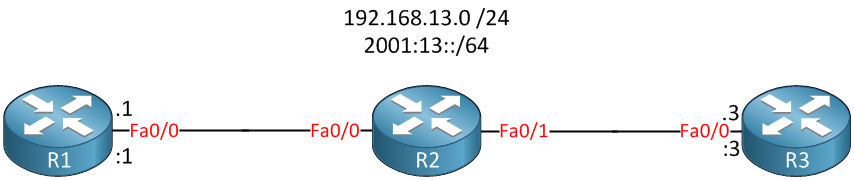
To demonstrate this feature I will use the following topology:
پیکربندی Zone Base Firewall(ترجمه فارسی بزودی در همین وبلاگ)
Zone Based Firewall Configuration Example
Zone Based Firewall is the most advanced method of a stateful firewall that is available on Cisco IOS routers. The idea behind ZBF is that we don’t assign access-lists to interfaces but we will create different zones. Interfaces will be assigned to the different zones and security policies will be assigned to traffic between zones. To show you why ZBF is useful, let me show you a picture:
ویژگی هایی در IOS های سیسکو که در صورت عدم نیاز باید آنها را غیر فعال یا محدود نمایید...
اخیرا با مروری که روی برخی ویژگی های IOS انجام شد مواردی مشخص گردید که ممکن است شما نیز روی روتر خود با آن مواجه شده باشید.
بسیاری از این ویژگی ها بصورت پیش فرض فعال هستند و می توانند امنیت شبکه شما را کاهش دهند.برای از بین بردن این ریسک شما می توانید آن هارا بررسی نموده و در صورت عدم نیاز آنها را غیر فعال یا محدود نمایید که لیست این ویژگی ها در ذیل ذکر شده است :
ادامه مطلب ...