(Network Administrators (Persian
نکات مهم شبکه برای متخصصین
(Network Administrators (Persian
نکات مهم شبکه برای متخصصینTransparent Cisco IOS Firewall(ترجمه فارسی بزودی در همین وبلاگ)
Transparent Cisco IOS Firewall
Cisco IOS routers can be configured as a layer 2 bridges, this means that you can configure two or more interfaces to be in the same layer 2 domain and that traffic will be switched instead of routed. Another feature that has been added since IOS 12.3(7)T is the transparent Cisco IOS Firewall. This allows traffic filtering and stateful inspection using CBAC for the layer 2 bridge.
When you configure the router as a transparent firewall it will not do any routing and will only learn the MAC addresses on the interfaces and switch frames between the interfaces. The advantage of a transparent firewall is that you can place it at any location in your network without having to change any IP addresses or networking settings like default gateways.
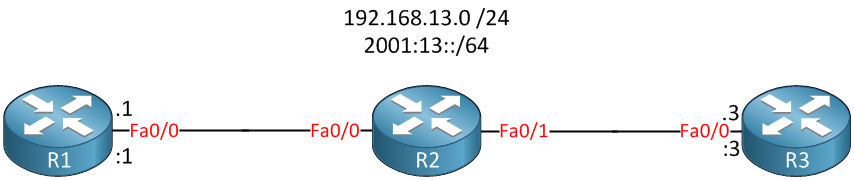
To demonstrate this feature I will use the following topology:
Above we have a small network with 3 routers…R1,R2 and R3. R2 will be configured to bridge its Fastethernet 0/0 and 0/1 interfaces together. This means that R1 and R3 will be in the same layer 2 domain.
R1 and R3 will use IPv4 subnet 192.168.13.0 /24 and IPv6 prefix 2001:13::/64. I will configure the firewall with the following requirements:
- R1 should be able to reach R3 using TCP, UDP and ICMP.
- R3 is not allowed to send anything to R1 with the exception of return traffic.
- IPv6 traffic between R1 and R3 is not allowed.
Let’s take a look how to achieve this!
Configuration
First we will configure R2 as a bridge. You have two options here:
- CRB (Concurrent Routing and Bridging)
- IRB (Integrated Routing and Bridging)
When you use CRB the router will act as a layer 2 bridge for all interfaces that are in the bridge group and all other interfaces will be layer 3.
With IRB you will be able to configure a BVI (Bridge Virtual Interface) for each bridge group. This is a layer 3 interface for the bridge group and you can compare it to the SVI (Switch Virtual Interface) on Catalyst switches. I’m not going to use any layer 3 services on R2 so I’ll choose CRB:
R2(config)#bridge crbBridging is now enabled. Let’s activate spanning-tree:
R2(config)#bridge 1 protocol ieeeThis will make the router run the IEEE version of spanning-tree. Let’s continue and add the two interfaces of R2 to the bridge group:
R2(config)#interface fastEthernet 0/0
R2(config-if)#bridge-group 1
R2(config)#interface fastEthernet 0/1
R2(config-if)#bridge-group 1This finishes our bridge configuration so we can continue with our transparent firewall configuration. First I’ll create an access-list that blocks all IP traffic:
R2(config)#ip access-list extended R3-TO-R1
R2(config-ext-nacl)#deny ip any anyWe’ll activate the access-list inbound on the link between R2 and R3:
R2(config)#interface fastEthernet 0/1
R2(config-if)#ip access-group R3-TO-R1 inTo make sure that R1 can reach R3 I’ll create some CBAC inspect rules:
R2(config)#ip inspect name CBAC tcp
R2(config)#ip inspect name CBAC udp
R2(config)#ip inspect name CBAC icmpThis should allow all TCP, UDP and ICMP traffic from R1 to R3. Let’s activate it inbound on the interface pointing to R1:
R2(config)#interface fastEthernet 0/0
R2(config-if)#ip inspect CBAC inBesides access-lists for IP and inspect rules I can also use protocol access-lists. This will help us to block IPv6 traffic:
R2(config)#access-list 200 deny 0x86DD
R2(config)#access-list 200 permit 0x0 0xFFFFWe’ll deny EtherType 086DD (IPv6) and permit all other EtherTypes. Let’s apply this protocol access-list to the bridge group:
R2(config)#interface fastEthernet 0/0
R2(config-if)#bridge-group 1 input-type-list 200
R2(config)#interface fastEthernet 0/1
R2(config-if)#bridge-group 1 input-type-list 200With the configuration above, R1 should be able to reach R3 using TCP, UDP or ICMP and IPv6 traffic should be blocked. Let’s find out if our configuration is working!
Verification
The first thing you should do is check if your bridge is operational and learning MAC addresses:
R2#show bridge
Total of 300 station blocks, 298 free
Codes: P - permanent, S - self
Bridge Group 1:
Address Action Interface Age RX count TX count
c200.23f6.0000 forward FastEthernet0/0 2 10 10
c202.23f6.0000 forward FastEthernet0/1 2 11 9R2 has learned the MAC addresses of R1 and R3. Let’s check our CBAC inspect rules:
R2#show ip inspect config
Session audit trail is disabled
Session alert is enabled
one-minute (sampling period) thresholds are [unlimited : unlimited] connections
max-incomplete sessions thresholds are [unlimited : unlimited]
max-incomplete tcp connections per host is unlimited. Block-time 0 minute.
tcp synwait-time is 30 sec -- tcp finwait-time is 5 sec
tcp idle-time is 3600 sec -- udp idle-time is 30 sec
tcp reassembly queue length 16; timeout 5 sec; memory-limit 1024 kilo bytes
dns-timeout is 5 sec
Inspection Rule Configuration
Inspection name CBAC
tcp alert is on audit-trail is off timeout 3600
udp alert is on audit-trail is off timeout 30
icmp alert is on audit-trail is off timeout 10Above we can see that TCP, UDP and ICMP will be inspected. Let’s send some traffic from R3 to R1 to see if our firewall works:
R3#ping 192.168.13.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.13.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)R2#show access-lists R3-TO-R1
Extended IP access list R3-TO-R1
10 deny ip any any (5 matches)We see matches in the access-list as R3 is hitting the ‘deny ip any any’. Let’s see if R1 can reach R3:
R1#ping 192.168.13.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.13.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/8/8 msR2#show ip inspect sessions
Established Sessions
Session 66E555E8 (192.168.13.1:8)=>(192.168.13.3:0) icmp SIS_OPENThat’s looking better, thanks to our inspect rules R1 can reach R3. What about IPv6? Will it be filtered?
R1#ping 2001:13::3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2001:13::3, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)R2#show access-lists 200
Type code access list 200
deny 0x86DD 0x0000 (28 matches)
permit 0x0000 0xFFFF (67 matches)As you can see IPv6 traffic is being blocked thanks to the protocol access-list. That’s all there is to it!
I hope this example helps you to understand the Transparent Cisco IOS Firewall. If you have any questions feel free to leave a comment!
 Copyright protected by Digiprove © 2013 Rene Molenaar
Copyright protected by Digiprove © 2013 Rene MolenaarRead more: http://networklessons.com/security/transparent-cisco-ios-firewall/#ixzz2luy2xTDs